How to Detect and Analyze DDoS Attacks Using Log Analysis Loggly
Command and control attacks, also referred to as C2 and C&C, are a type of attack in which a malicious actor uses a malicious server to command and control already compromised machines over a network. The malicious server (the command and control server) is also used to receive the desired payload from the compromised network.

How to DDOS with CMD YouTube
Open the Notepad app. Copy and paste the following commands. :loop. ping
Dos/DDos Attacks InfosecTrain
Best DDoS Attack Script Python3, (Cyber / DDos) Attack With 56 Methods. A versatile command and control center (CCC) for DDoS Botnet Simulation & Load Generation. bot ddos dos bots botnet simulation ccc denial-of-service ddos-tool commandandconquer botnets ddos-attack-tools ddos-attack attack-simulator commandandcontrol attack-simulation
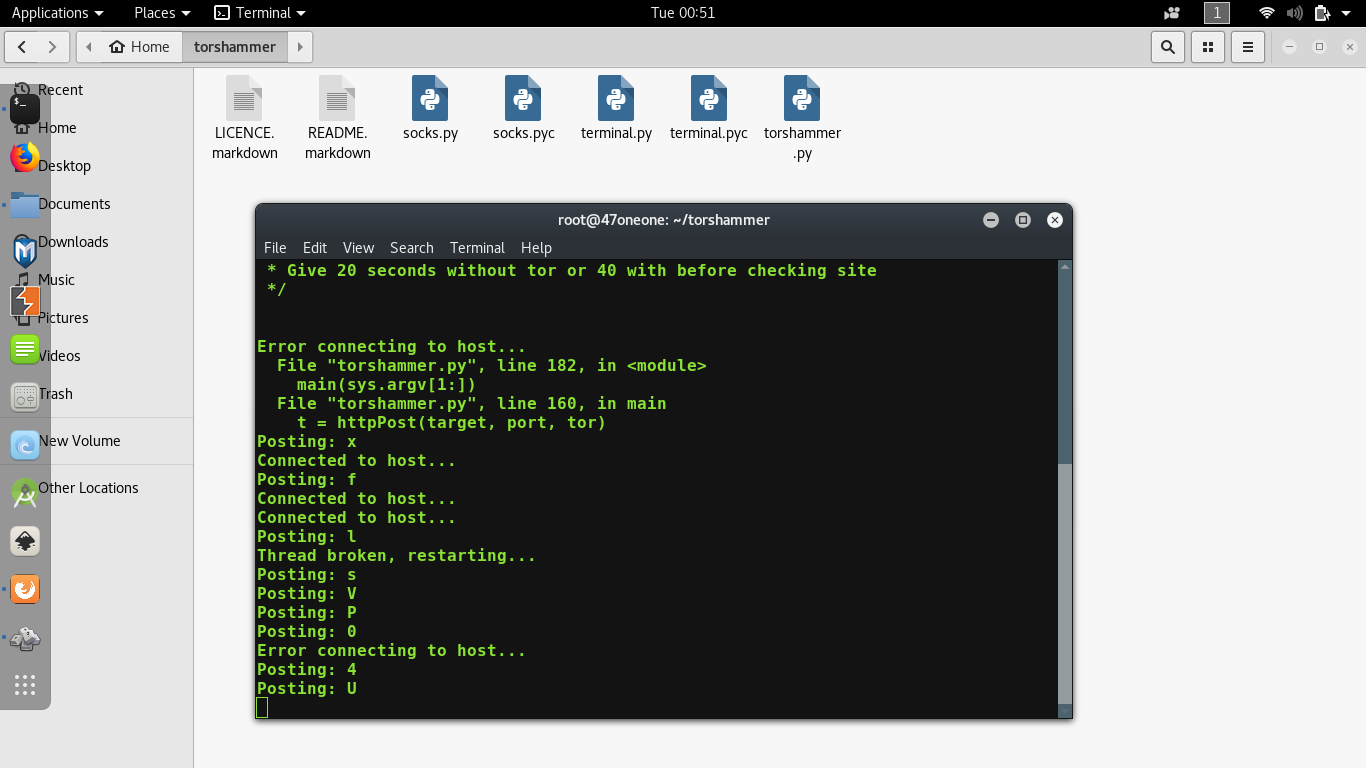
Perform DDoS attack using Torshammer
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are malicious attempts to disrupt the normal operations of a targeted server, service, or network by overwhelming it with a flood of Internet traffic. DoS attacks accomplish this disruption by sending malicious traffic from a single machine — typically a computer.
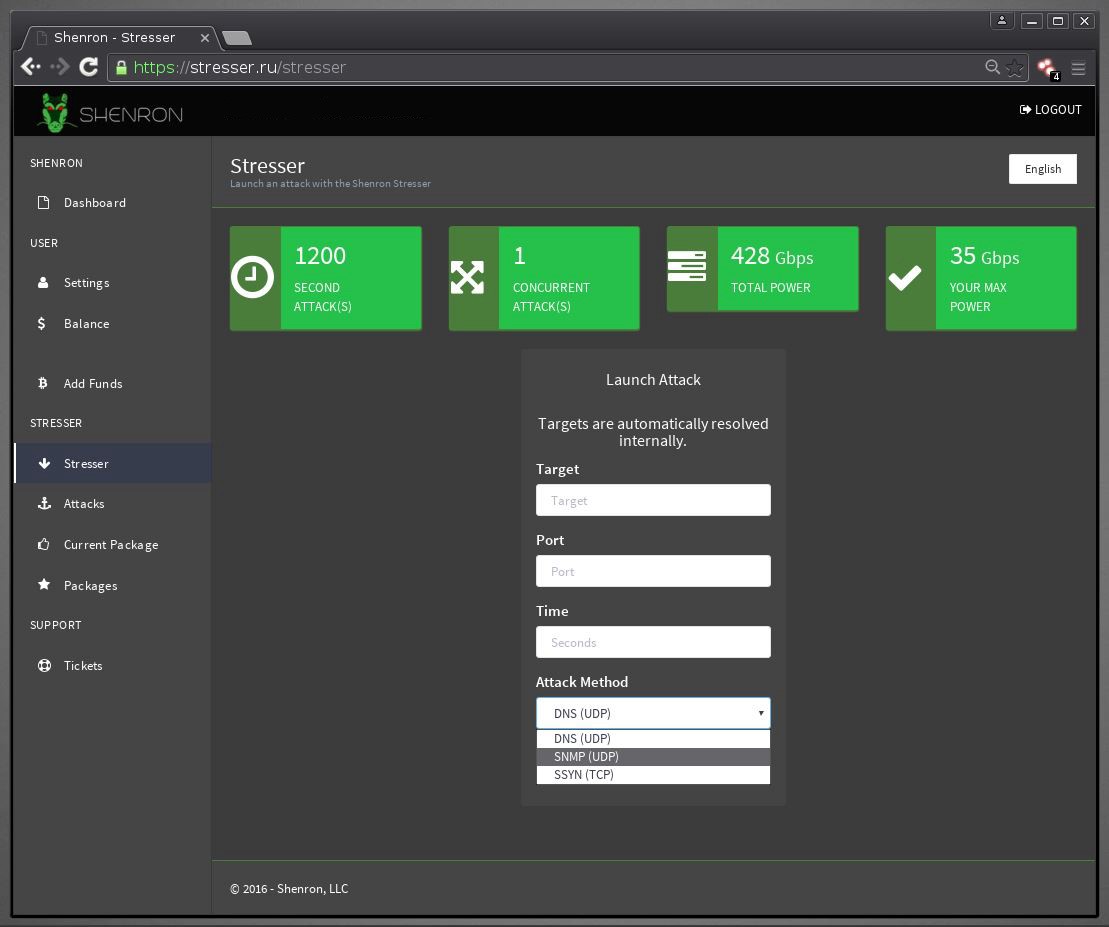
DDoS Attacks via DDoS as a Service Tools
Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system.

Johny Blog DDoS attack using hping Command in Kali Linux
These commands, combined with the previously mentioned ones, offer a comprehensive toolkit for preventing and stopping DDoS attacks at the application layer. Implementing these commands and adopting a proactive defense approach will enhance your network security and resilience against DDoS threats.
Ddos Attack Cmd news word
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic.

How To Ddos with CMD (Beginners) YouTube
The attacker will use the ping command on the command line to create a ping of death packet. The options parameter is crucial, as its value establishes the size of the ICMP data field. On Windows systems, the option is found under "-l" for load.. Instead of disrupting central network devices with DDoS attacks or sneaking through onto.

Ddos Attack .rDos. & CMDBy AxY YouTube
Discover how a ping of death command works and how to protect your organization from ping of death and DDoS attacks. The ping of death is a form of denial-of-service (DoS) attack that hackers use to crash or freeze computers, services, and systems.. Attackers use ping commands to develop a ping of death command. They can write a simple loop.
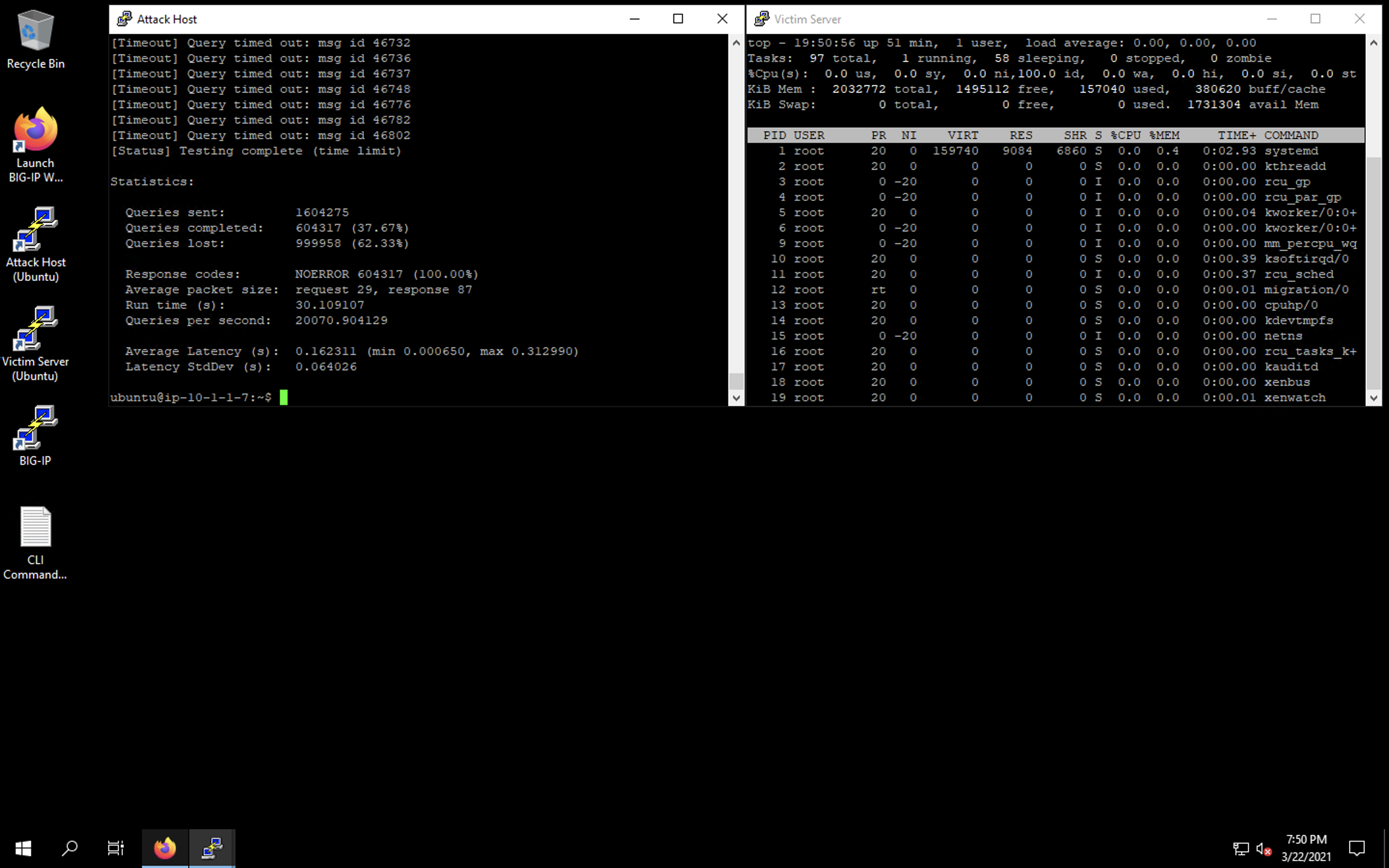
Simulate a DNS DDoS Attack
Open the command prompt on the target computer. Enter the command ipconfig. You will get results similar to the ones shown below. For this example,. DDoS attack is an escalated form of a DoS attack where the malicious traffic comes from multiple sources - making it harder to stop the attack simply by blocking a single source..
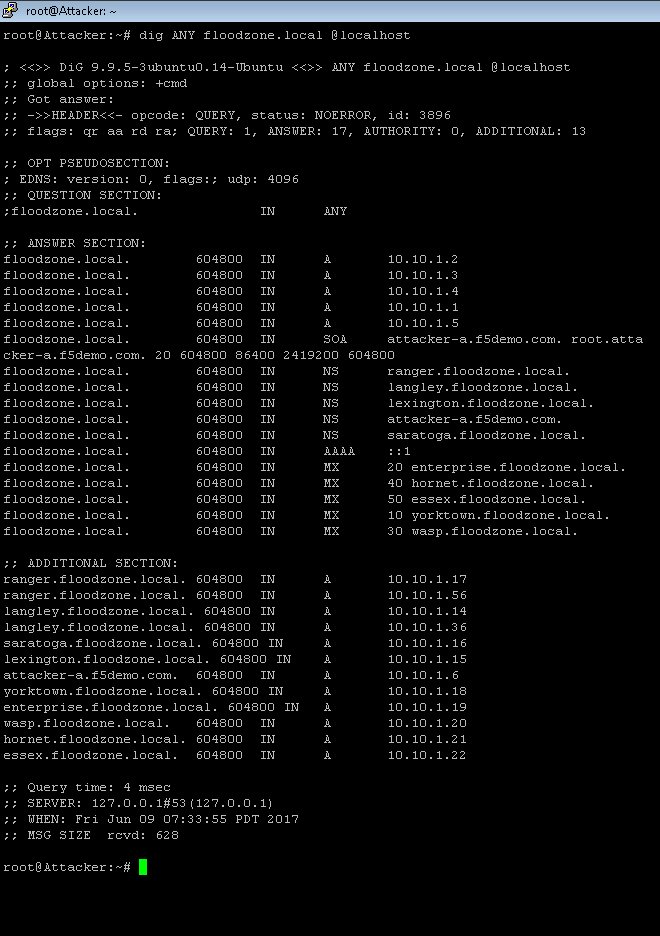
Ddos Attack Cmd news word
ping www.google.com -t. Note: Replace www.google.com with the website on which you want to perform the DDoS attack. c. You will see the IP address of the selected website in the result. Note: IP address will look like: xxx.xxx.xxx.xxx. 3. After getting the IP address, type the below command in the command prompt.
Tutorial Cara Mudah DDOS Attack Hanya Dengan Program Prompt
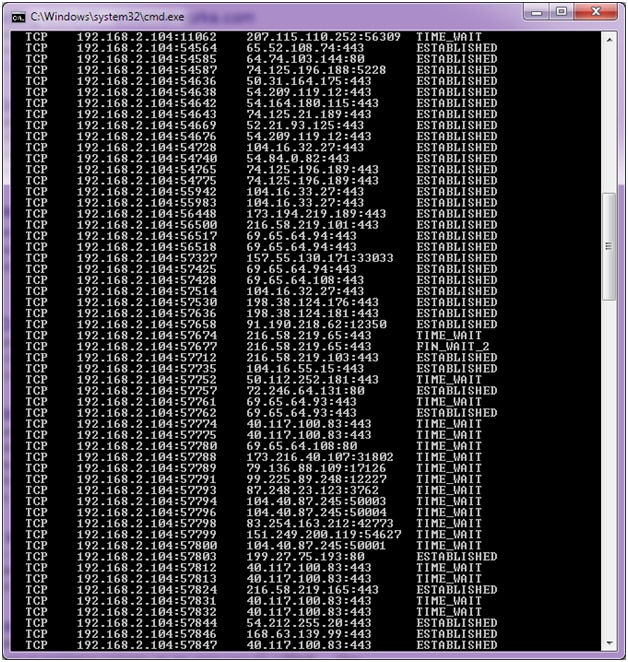
Useful in detecting a single flood by allowing you to recognize many connections coming from one IP. #netstat -n -p|grep SYN_REC | wc -l. To find out how many active SYNC_REC are occurring on the server. The number should be pretty low, preferably less than 5. On DoS attack incidents or mail bombs, the number can jump to pretty high.
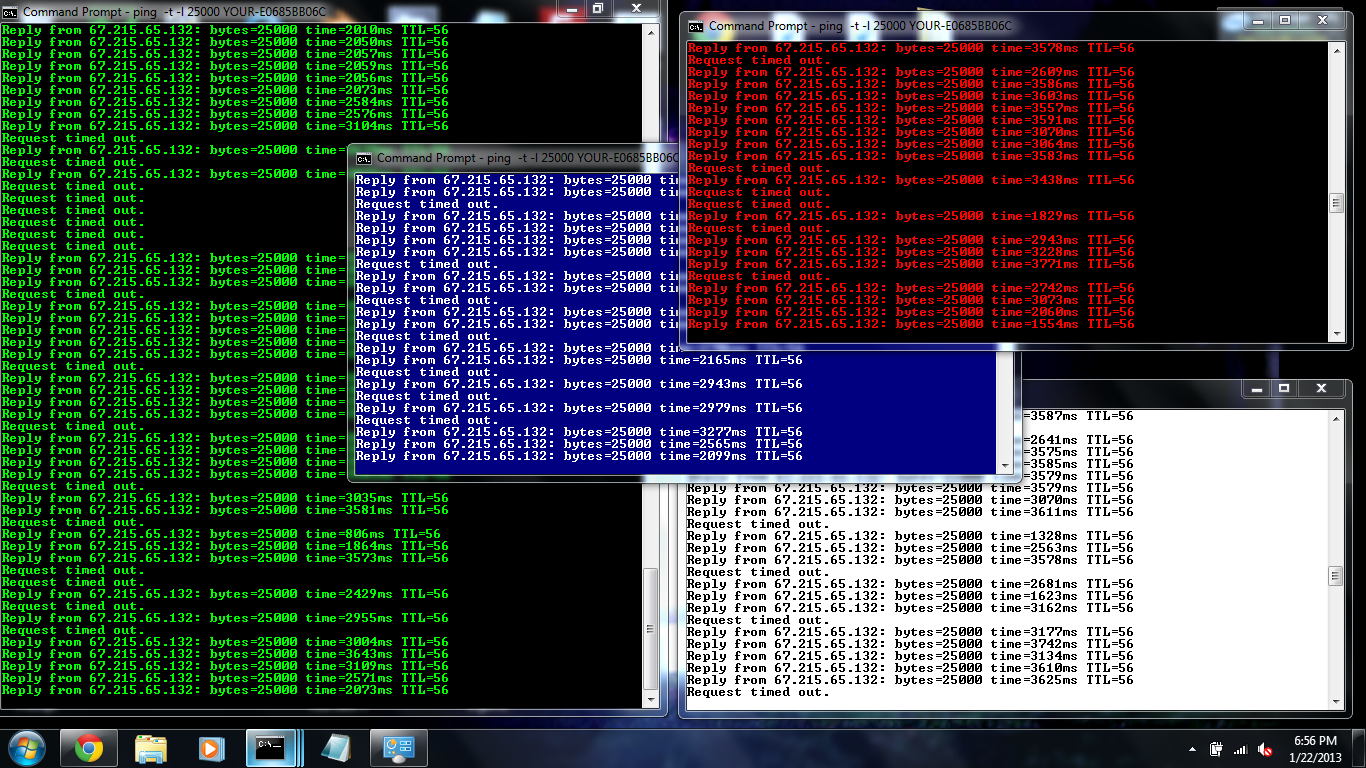
How to perform DDos attack using CMD DR Hacker4U
A ping flood is a denial-of-service attack in which the attacker attempts to overwhelm a targeted device with ICMP echo-request packets, causing the target to become inaccessible to normal traffic. When the attack traffic comes from multiple devices, the attack becomes a DDoS or distributed denial-of-service attack.
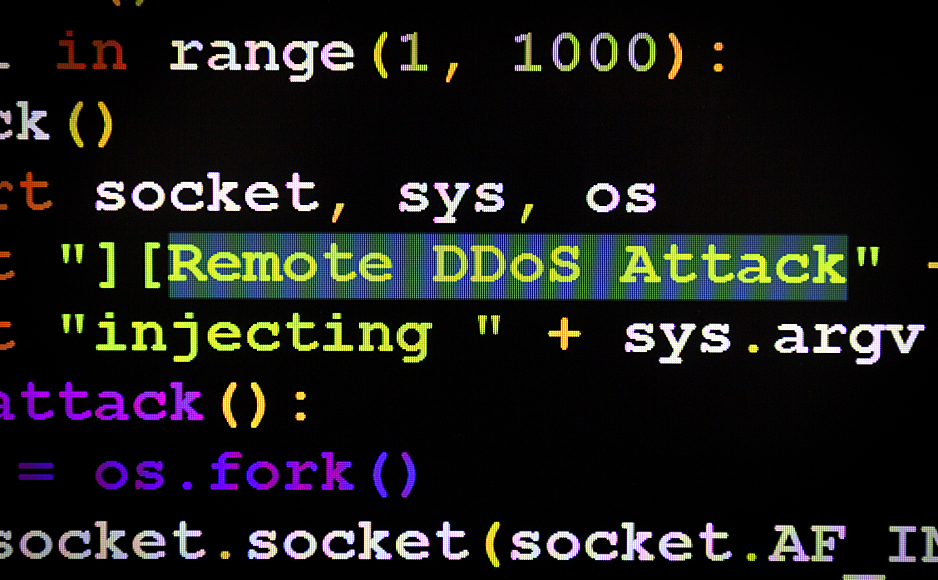
Powerful ddos attack tool peacedarelo
Step 1: Block their IP address. This is assuming that this is a DoS attack (coming from 1 IP address.). Use tools like Wireshark to see where this attack is coming from. Then use online tutorials on how to block IP addresses on your firewall. Block the attacker on any P2P (peer to peer) applications (like Skype) so they cannot find your IP.
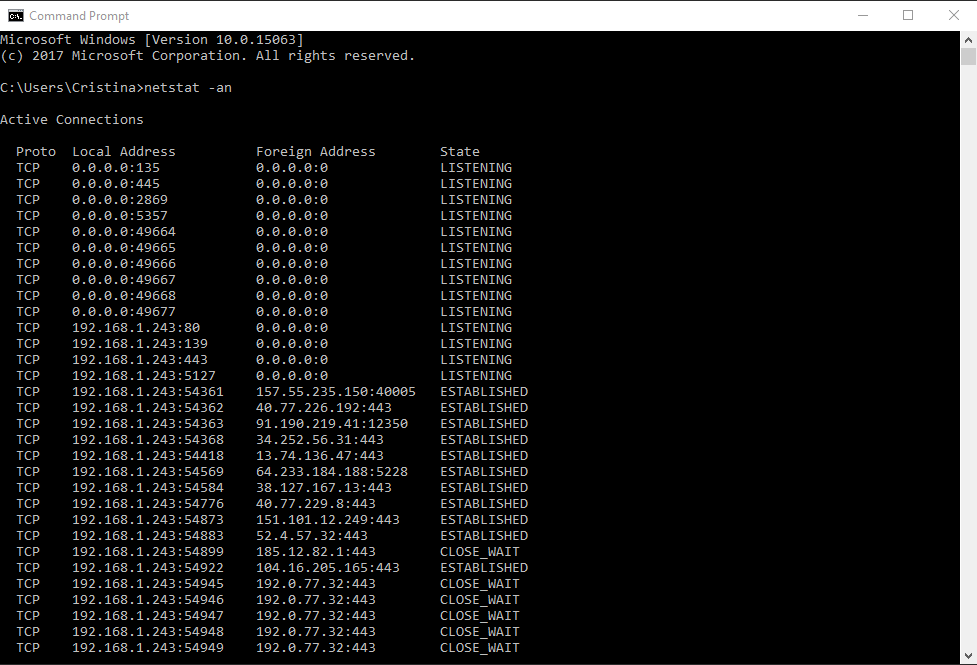
How To Ddos Using Cmd Stanley Lepaso
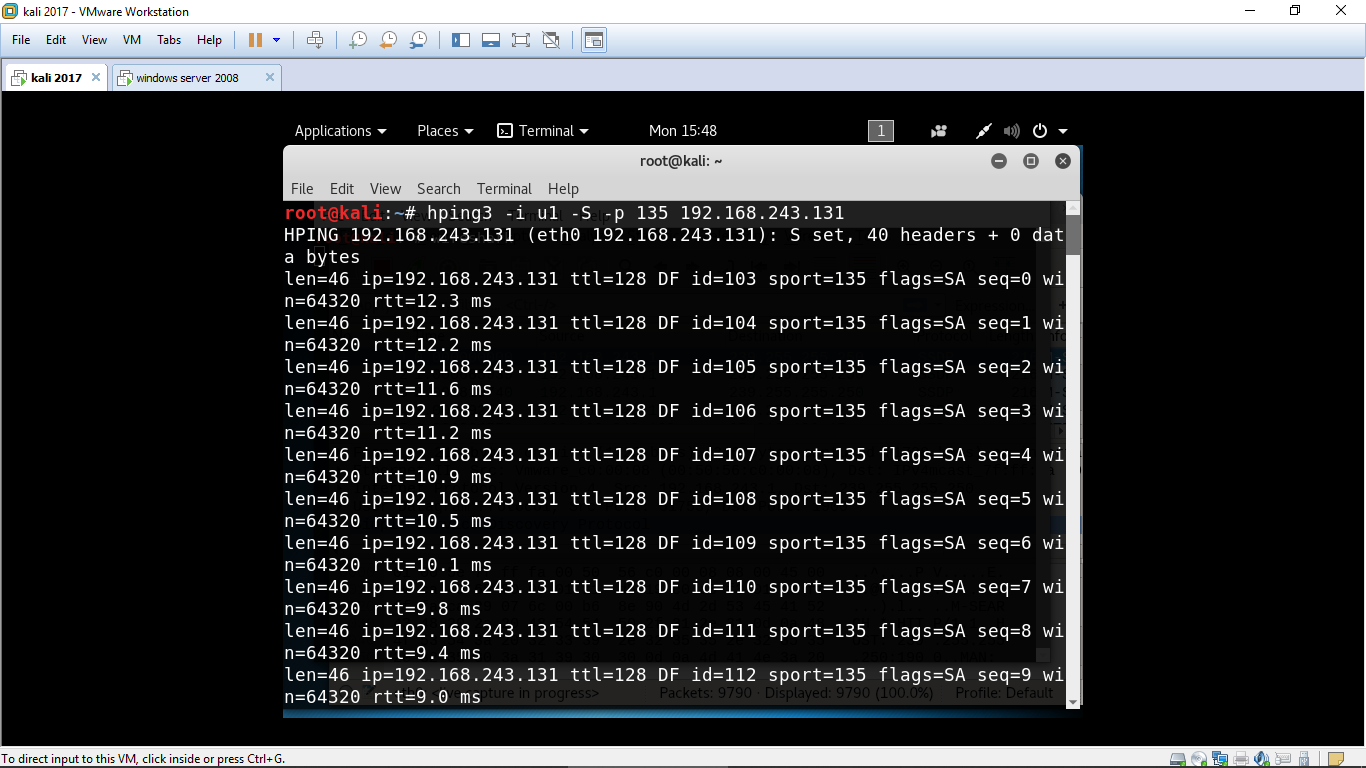
Denial-of-service Attack - DoS using hping3 with spoofed IP in Kali Linux. In computing, a denial-of-service ( DoS) or distributed denial-of-service ( DDoS) attack is an attempt to make a machine or network resource unavailable to its intended users. Although the means to carry out, the motives for, and targets of a DoS attack vary, it.
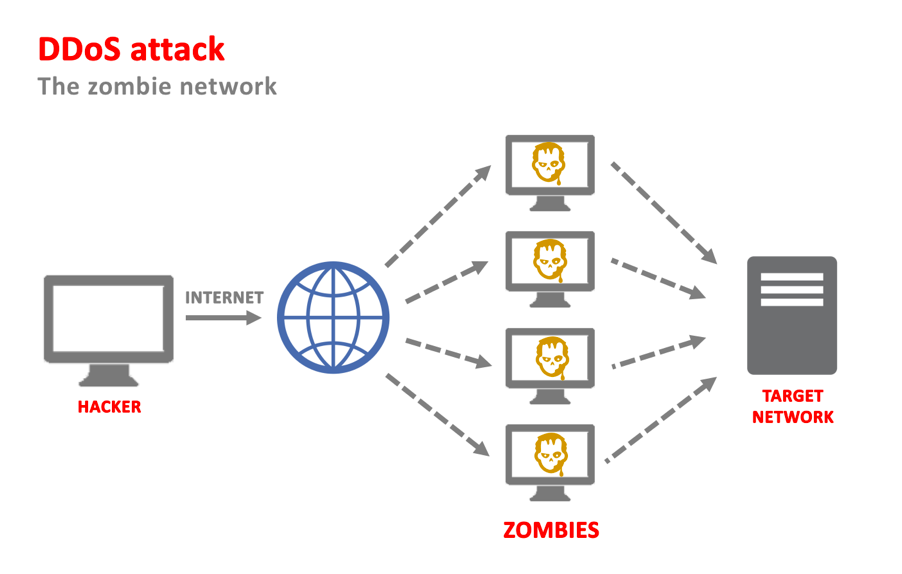
Dos and DDos attack
A dedicated server with DDoS protection is prepared to continue working without disruptions in availability. Use the route command to block the attacker's IP address. sudo route add [ip-address] reject. Note: The route command is part of the net-tools package. To install it on Ubuntu, type: